Resourcely has added a free tier option for its platform for safely configuring and deploying cloud resources using a set of templates and guardrails for application developers using either open source Terraform or OpenTofu infrastructure-as-code (IaC) tools.
Company CEO Travis McPeak said the platform makes it possible for DevOps teams to centrally govern the configuration of cloud resources in a way that doesn’t adversely impact application developer productivity.
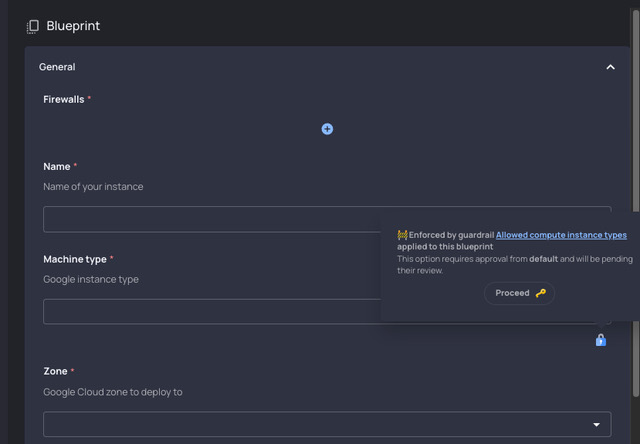
Using a set of blueprints that are managed via the Resourcely platform, DevOps teams can embed policies into workflows that prevent application developers from misconfiguring cloud infrastructure resources, he said. The platform generates code that is submitted like any other pull request managed by a continuous integration/continuous delivery (CI/CD) platform.
The free tier includes access to a proprietary Knowledge Graph that collects data about cloud services and their properties. DevOps teams can use that data to pre-populate and auto-fill instances and regions to provide developers with self-service capabilities.
Resourcely is also providing early access to a Campaign capability that enables DevOps teams to define configuration standards, identify and track resources in violation, and automatically generate Terraform code that remediates misconfigured infrastructure.
Longer term, Resourcely intends to also add support for YAML files used to configure Kubernetes clusters as well as the other automation framework such as Ansible and Cloud Formation from Amazon Web Services (AWS).
Given the myriad options developers are presented with when configuring cloud resources, it’s simply too easy for them to make a mistake that might, for example, leave a port open through which cybercriminals can export data, noted McPeak. Resourcely enables organizations to ensure that best DevSecOps practices are being followed, he added.
Naturally. Resourcely hopes that organizations using its free tier will eventually migrate to the more robust paid service plans the company already provides. Many of the cloud security issues that organizations encounter can be traced back to lack of understanding of the shared responsibility model that cloud service providers have imposed. While the cloud service provider is responsible for securing their infrastructure, the security of the applications and the code used to configure those platforms is the responsibility of organizations that are now deploying software at scale in the cloud.
Unfortunately, many application developers still tend to assume that cloud service providers are automatically securing configuration code on their behalf, and in the absence of any effort to secure that code, many organizations are providing cybercriminals with a relatively simple method to compromise their software supply chains. As such, DevOps teams are under more pressure than ever to improve cloud security hygiene, noted McPeak. The challenge is making sure that DevOps teams, for want of a few simple policies that were not being enforced, don’t make it too easy for cybercriminals to achieve their aims, he added.
It’s not clear how often cloud services are being compromised because of misconfigurations versus, for example, cybercriminals simply stealing the credentials of a developer. Regardless of how a cloud computing environment is compromised, it’s apparent that as more workloads are deployed in the cloud there are more attempts with each passing day being made to create a breach.




